Exploit Fix
Exploit Fix
Mojang announcement regarding this vulnerability: IMPORTANT MESSAGE: SECURITY VULNERABILITY IN JAVA EDITION
On December 9, 2021 an exploit was found on one of the logging libraries being used by Minecraft server jars. This is an RCE (Remote Code Execution) vulnerability, so it's considered severe and everyone is advised to update as soon as possible.
A fix for the exploit for Paper was released by the PaperMC team and subsequently was merged by the different forks of Paper. Other server jars have also released builds implementing a fix.
On December 10, 2021 Mojang released a fix for the exploit on Minecraft clients and steps on how to fix it on older versions of Minecraft servers. Follow the steps outlined below to fix the exploit.
Clients also were vulnerable to this exploit, but Mojang has already released a patch that applies to all Minecraft versions - You just need to close all running instances of the game and the Minecraft launcher and start the lancher again - The patched version will download automatically.
It's not recommended to play on servers that haven't been updated to the latest version of Minecraft, as they may be vulnerable to the exploit. This is critical for modded clients that didn't received the fix Mojang has released. So make sure you also update your click and verify with them if they have released a patch to the exploit.
We have created this document to guide you through the steps to fix the exploit. We recommend you apply the flag if needed for your Minecraft version and update your server jar to the latest build available, make sure this build includes a fix for the exploit (it should say so in the changelog). Steps on how to do both things are listed below.
If you need help doing any of this please refer to our #support-chat channel on our Discord server.
If your server is running:
Forge servers
Forge has published an extensive article detailing steps on how to fix the exploit either by updating to the latest build or by applying a flag. You can read more here.
1.18 servers (Vanilla, Spigot, Paper, Purpur and other forks)
1.18: Upgrade to 1.18.1, if possible. If not, use the same approach as for 1.17.x:
Link to PaperMC 1.18.1 .jar with the fix to the exploit:
- Paper 1.18.1 - Choose the latest build on the website and download it: PaperMC 1.18.1 Builds
1.17 - 1.17.1 servers
We have already applied the fix to all servers running 1.17+. We still recommend you upgrade to the last build of 1.17.1 or 1.18.1.
Links to PaperMC 1.17.1 jars with the fix to the exploit:
- Paper 1.17.1 - Choose the latest build on the website and download it: PaperMC 1.17.1 Builds
If you update to one of the builds listed above you don't need to apply the flag fix we are listing below.
If you still want to apply the fix, follow the steps listed below:
Mojang has recommended you add the -Dlog4j2.formatMsgNoLookups=true flag to your startup command. On December 9, 2021 the Bloom.host team added this flag to all Minecraft servers, so you just have to make sure you have this flag in your startup command. Also, make sure to restart your server, if you haven't done recently since restarting the server applies the flag on startup. To verify that you have the flag, just go to Minecraft panel, then go to the startup tab and make sure the flag is on the startup command, it should be before the -jar text. It's also recommended you update to the latest build of 1.17.1 provided by your server jar. Paper, Fabric and other server jars have released builds of 1.17.1 including the exploit fix. Refer to the updating section at the end of this document for more information.
1.12 - 1.16.5 servers
PaperMC has released jars with the fix for the exploit. These jars are not in their website, here are are direct links to them (You can also find it on our server type selector on the settings tab):
Official statement from PaperMC: All legacy builds are unsupported. There may be some console or other issues on some servers. Download and use at your own risk. Legacy build links:
-
Paper 1.16.5 Build #792 - Click here to download
-
Paper 1.15.2 Build #392 - Click here to download
-
Paper 1.14.4 Build #244 - Click here to download
-
Paper 1.13.2 Build #656 - Click here to download
-
Paper 1.12.2 Build #1619 - Click here to download
If you update to one of the builds listed above you don't need to apply the flag fix we are listing below.
If you still want to apply the fix, follow the steps listed below:
We have added an easier way to install this fix. Just go to the settings tab on your server and under the "FIX MINECRAFT LOG4J VULNERABILITY" section, click on the Minecraft Version 1.12-1.16 button to apply the fix, then restart your Minecraft server.
If for any reason your server doesn't starts after applying the fix or you want to remove the fix click on the Remove.
If for any reason you need to do this manually, follow the steps below:
Download this file to the home directory where your server runs. To do this you can go to the URL and it will open a .xml file on your browser, you will have to right click then click on 'Save as' then save the .xml file. You can also head over to the File Manager on our Minecraft panel, click on the Download from URL button and paste the following URL: https://launcher.mojang.com/v1/objects/02937d122c86ce73319ef9975b58896fc1b491d1/log4j2_112-116.xml and this will download the file to the home directory of your server. After the file is on the server, go to the startup tab on the Minecraft panel add the following JVM arguments to your startup flags. To do this just go to the startup tab and add the following JVM arguments in the startup flags box: -Dlog4j.configurationFile=log4j2_112-116.xml. After you have added the JVM arguments, restart your server. It's also recommended you update to the latest build provided by your server jar. Most developers have expressed their intention to not updating oldest versions server jars to include the exploit fix, but Paper has already issued a new build of 1.16.5 (Build #792) that includes the bug fix. Refer to the updating section at the end of this document for more information.
1.7 - 1.11.2 servers
PaperMC has released jars with the fix for the exploit. These jars are not in their website, but here are direct links to them (You can also find it on our server type selector on the settings tab)
Official statement from PaperMC: All legacy builds are unsupported. There may be some console or other issues on some servers. Download and use at your own risk. Legacy build links:
-
Paper 1.11.2 Build #1105 - Click here to download
-
Paper 1.10.2 Build #917 - Click here to download
-
Paper 1.9.4 Build #774 - Click here to download
-
Paper 1.8.8 Build #444 - Click here to download
If you update to one of the builds listed above you don't need to apply the flag fix we are listing below.
If you still want to apply it (from our test, this flags don't work with Paper 1.7 - 1.11.2 and your server will not start if you use them) you can follow this steps:
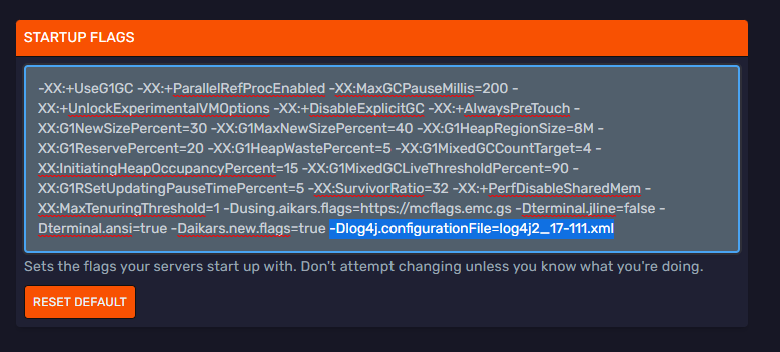
Download this file to the home directory where your server runs. To do this you can go to the URL and it will open a .xml file on your browser, you will have to right click then click on 'Save as' then save the .xml file. You can also head over to the File Manager on our Minecraft panel, click on the Download from URL button and paste the following URL: https://launcher.mojang.com/v1/objects/dd2b723346a8dcd48e7f4d245f6bf09e98db9696/log4j2_17-111.xml and this will download the file to the home directory of your server. After the file is on the server, go to the startup tab on the Minecraft panel add the following JVM arguments to your startup flags. To do this just go to the startup tab and add the following JVM arguments in the startup flags box: -Dlog4j.configurationFile=log4j2_17-111.xml. After you have added the JVM arguments, restart your server.
1.6 and below servers
Servers running versions 1.6 and below are not affected by this exploit.
Adding the flag to the startup flags section
Example of how to add the flag to your startup command (see highlighted text). Remember that you need to add the appropiate flag that matches your Minecraft server version.
Updating your server jar to the latest build
✅ Spigot - See here!
✅ Paper - Download here - The exploit fix is in Build #64 or newer for MC 1.18 / Build #398 or newer for MC 1.17.1. Paper has also backported the fix to MC 1.16.5 with Build #792 which can be found here. We recommend the use of Build #399 or newer for MC 1.17.1 and Build #67 or newer for MC 1.18-1.18.1, these builds are the ones that include an updated Log4J library (the library which had the exploit on older versions).
PaperMC builds that include the exploit fix:
-
Paper 1.18.1 - Choose the latest build on the website and download it: PaperMC 1.18.1 Builds
-
Paper 1.17.1 - Choose the latest build on the website and download it: PaperMC 1.17.1 Builds
-
Paper 1.16.5 Build #792 - Click here to download
-
Paper 1.15.2 Build #392 - Click here to download
-
Paper 1.14.4 Build #244 - Click here to download
-
Paper 1.13.2 Build #656 - Click here to download
-
Paper 1.12.2 Build #1619 - Click here to download
-
Paper 1.11.2 Build #1105 - Click here to download
-
Paper 1.10.2 Build #917 - Click here to download
-
Paper 1.9.4 Build #774 - Click here to download
-
Paper 1.8.8 Build #444 - Click here to download
✅ Purpur - Download here - The exploit fix is in Build #1432 or newer for MC 1.18.
✅ Waterfall - Download here - The exploit fix is in Build #467 or newer. We recommend the use of Build #468 or newer which includes an updated Log4J library (the library which had the exploit on older versions).
✅ Velocity - Download here - The exploit fix is in Build #97 or newer. We recommend the use of Build #98 or newer which includes an updated Log4J library (the library which had the exploit on older versions).
✅ Forge - Download here - Forge has updated the most popular versions to apply the exploit fix. The following Forge versions (or newer versions) are the ones that contain the exploit fix:
Forge has published an extensive article detailing steps on how to fix the exploit either by updating to the latest build or by applying a flag. You can read more here.
- 1.18-38.0.17 or newer
- 1.17.1-37.1.1 or newer
- 1.16.5-36.2.20 or newer
- 1.15.2-31.2.56 or newer
- 1.14.4-28.2.25 or newer
- 1.13.2-25.0.222 or newer
- 1.12.2-14.23.5.2857 or newer
You should be able to download one of the jars above (make sure you download a build with the fix), run the .jar on your machine, click on create server files, then archive/zip all the server files that were generated and upload them to your server.
You can also update your server using our Server Type selector. Just go to the settings page on your server, then select the jar you want to download and select the latest build. Make sure you reference the build # listed above so you know you are downloading a build that includes the fix. You may also make use of an Update to the latest build button if you have used our Server Type selector in the past.
It's recommended you run a server backup before updating or doing any changes. Check our guide on How backups works and how to use them.
How to verify if your server is vulnerable
As per PaperMC team: To test if the patch is working, run say ${date:YYYY} in console, it should output the same command and not 2021. If it outputs 2021 you have not fixed the issue properly.
If you need help updating your server please refer to our Updating guide and #support-chat channel.